
Artificial Intelligence (AI) has been a significant factor in this advancement, and its use by malicious actors has increased exponentially in recent years. An example of this and the subject of this blog post is the "BlackMamba" keylogging attack, which leverages AI to evade modern Endpoint Detection and Response (EDR) systems.
More than 60% of global financial institutions with at least $5 billion in assets were hit by a variety of cyberattacks over the past year, according to a new survey by Contrast Security. Incidents included attempts to destroy data held by the institutions, usually to erase evidence following a counter-incident response by the victim. In addition, "watering hole" attacks in which cybercriminals hijack and boobytrap a website or mobile app used by e-finance customers. Sixty-four percent of institutions also reported increased attacks exploiting application vulnerabilities; thus, the threat appears to be growing and needs to be defended more effectively.
BlackMamba is a malware known to target financial institutions in various European countries, including Germany and the Czech Republic. The malware can remain hidden from detection systems and infiltrate targeted systems via phishing campaigns or software vulnerabilities. Once installed, the malware can steal sensitive information such as passwords and user credentials, ultimately leading to financial theft.
With malware like 'BlackMamba,’ a cybercriminal can deploy a series of typically highly detectable behaviors in a non-typical combination and evade detection by exploiting the technologies inability to recognize it as a malicious pattern. It is unique because the BlackMamba malware is truly polymorphic and can change its signature to avoid detection. This problem is compounded when artificial intelligence is added to the malware. The bottom line is that the malware's method of behavior is highly atypical compared to those used by the traditional types of attacks by human threat actor counterparts. Additionally, the speed at which these attacks can be executed makes the threat exponentially worse.
The introduction of ChatGPT last year marked the first-time neural network code synthesis was offered free to the public. ChatGPT is the brainchild of the AI research and development company OpenAI. HYAS Institute researcher and cybersecurity expert Jeff Sims has developed a new ChatGPT-powered malware called Blackmamba, which can bypass Endpoint Detection and Response (EDR) filters.
This should not come as a surprise, as cybersecurity researchers at CyberArk reported on how ChatGPT could be used to develop polymorphic malware in January of this year. During their investigation, the researchers created the polymorphic malware by bypassing the content filters in ChatGPT, using an authoritative tone.
Researchers from HYAS Labs demonstrated the proof-of-concept attack, which they call BlackMamba, which exploits a large language model (LLM) — the technology on which ChatGPT is based — to synthesize a polymorphic keylogger functionality on the fly. The attack is "truly polymorphic" in that every time BlackMamba executes; it resynthesizes its keylogging capability, the researchers wrote.
According to the company's CEO, just five days after its launch on November 2022, it amassed over 1 million users. That's fast when you consider that it took Instagram 75 days to reach 1 million users, ten months for Facebook, 24 months for Twitter, and 41 months for Netflix.
ChatGPT is a versatile and powerful tool used for everything from answering simple questions to writing a blog post like this, composing essays and articles, and developing original software programs, including malware. From an IT security perspective, traditional security solutions like EDRs leverage multi-layer data intelligence systems to stop even the most sophisticated threats.
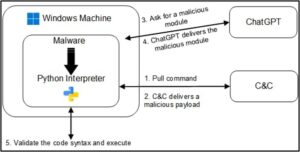
The BlackMamba attack is a malicious keylogger that uses AI-driven methods to evade detection by modern EDR systems. It starts with an initial payload designed to bypass traditional security measures like antivirus software and firewalls. Once it has successfully infiltrated the system, it begins collecting keystrokes from the user. This data is then sent back to the attacker for analysis using AI algorithms.
BlackMamba is an entirely new breed of malware, generating new, unique, and benign code each time using AI. The sinister and perhaps clever part of BlackMamba is that it uses AI-driven methods to identify which keystrokes are significant and which are not automatically. For example, suppose the user types their name or addresses into a web form. In that case, BlackMamba will recognize this as important data and send it back to the attacker while ignoring other keystrokes like typing emails or chatting with friends on social media platforms. This makes it harder for EDR systems to detect the attack because there is no single "smoking gun" they can identify; instead, they must analyze large volumes of data over time to find any evidence of malicious activity.
Using its built-in keylogging ability, BlackMamba can collect sensitive information, such as usernames, passwords, credit card numbers, and other personal or confidential data that users type into their devices. Upon capturing the data, BlackMamba uses Microsoft Teams webhook to send the collected data to the malicious MS Teams channel, which can be analyzed, sold on the dark web, or used for other criminal purposes.
AI is intended to overcome two challenges the authors perceived were fundamental to evading detection. First, by retrieving payloads from a "benign" remote source rather than an anomalous C2, analysts hope that BlackMamba traffic will not be seen as malicious. Second, by leveraging a generative AI that could deliver unique malware payloads each time, they hoped that security solutions would be tricked into not being able to recognize the returned code as malicious.
BlackMamba executes the dynamically generated code it receives from the AI within the context of the benign program using Python's exec() function. The malicious polymorphic portion remains in memory, which has led BlackMamba's creators to claim that existing EDR solutions difficulty detecting the malware with traditional security tools.
Most anti-virus software and intrusion detection systems (IDS) attempt to locate malicious code by searching through computer files and data packets sent through a network. If the security solution identifies patterns corresponding to known computer viruses, worms, or other malware, it takes appropriate steps to neutralize the threat. Polymorphic algorithms make it difficult for such software to recognize the offending code because it constantly mutates.
Fortunately, you can take steps to protect against the BlackMamba attack. The most important is ensuring your EDR system is up-to-date with the security vendor's latest security patches and updates. Additionally, you should also monitor your network traffic for anomalous behavior, such as sudden spikes in bandwidth usage or unusually high numbers of outbound connections from specific devices on your network. Finally, ensure all users on your network have strong passwords that are changed regularly; using best practices concerning password management will make it harder for attackers to gain access through brute force attacks or phishing attempts.
The Blackmamba malware has caused significant damage to various businesses, including financial losses and damage to their reputation. While the threat posed by BlackMamba should not be underestimated, taking these simple steps can help keep your business safe from this new type of attack vector powered by artificial intelligence (AI). By staying vigilant and ensuring your EDR system is up-to-date with the latest patches and updates, you can significantly reduce your risk of becoming a victim of BlackMamba or any other malicious cyber attacks powered by AI technology.