
The Evolution of Ransomware from the Eyes of Cyber Intelligence Threat Experts
Cyber threat intelligence experts are consistently trying to identify new strains of malware, track its evolution and for the benefit of all of us, and attempt to anticipate attack vectors as well as potential victims. This blog post leverages the insights of two Cyber Threat Intelligence Experts, both with years of experience tracking the evolution of cyberthreats and cybercriminals, and for our article, the evolution of ransomware. Thus, in this article, you can expect guidance on responding to threats, managing events and incidents and handling ransom demands. Before we dig into the ransomware threat landscape, I’ll introduce our threat intelligence experts Tom and Ben.
Ben is a Cyber Threat Intelligence Expert with a focus on media intelligence. Ben has 25 years of experience covering political, strategic, operational, and tactical industry issues. Ben started as a military officer; after his military career, he became a threat/risk strategic senior advisor for news organizations and current affairs. He is now Cyber Threat Intelligence expert with Hitachi Systems Security focusing on malware evolution and state sponsored cyber threat intelligence and attack trends.
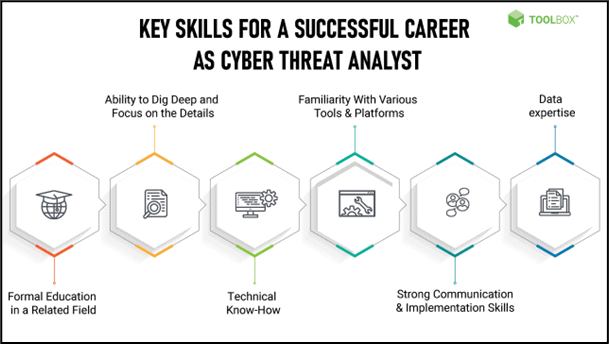
Figure 1 - Cyber Threat Intelligence Analyst/Expert Critical Skills
Tom is a Cyber Threat Intelligence Expert with a focus on threat watch and techno bulimic. He started in systems and network security as an engineer and now has shifted his focus to IT security leadership. He has earned several C-level roles within companies like Bell, Africa EXN, and is now here at Hitachi Systems Security in a C-level role.
A Cyber threat intelligence analyst or expert is an information security professional who leverages skills and expertise of network engineering to mitigate and avoid cyberattacks on the organization or its employees. They identify vulnerabilities and conduct digital forensics and threat modeling to monitor and tackle threats against organizational infrastructure
Ben and Tom’ Key Observations Include:
Cyber Threat Intelligence Experts’ Perspective on the Increase in Ransomware Attacks
We asked Ben and Tom why ransomware has become the most prominent threat in security over the past 2-3 years. Ben suggests, "Recon data is only getting easier to gather as an increasing amount of information is available online about companies. Further, that data is used for phishing and other types of attacks that leverage social engineering to breach a system or device."
Tom added, "It has become easier for enterprises to pay the ransom than the annual expense of improving their security posture." We wrote a blog post titled, Protect Your Organization from Ransomware With A 4-Step Approach; in the post we leveraged data from the benchmark Verizon Data Breach Survey which said the following:
Technology advancements are making security team operations more expensive for organizations to run in-house as SOC’s and IT security teams now require more advanced toolsets as well as highly skilled professionals. From the average organization’s perspective, paying a $100,000 ransom fee if far less expensive than spending hundreds of thousands of dollars to upgrade its security posture with leading edge security technology, additional SOC analysts and other security personnel.
How is Ransomware Deployed so Successfully?
Next, we asked how Ransomware is typically deployed to make attacks against even the most prepared organizations so successful. Ben and Tom both agreed that phishing is still the number one attack vector used by cyber criminals. They further suggested that while e-mail phishing attacks still top the list of social engineering attacks, smishing and vishing are increasingly used successfully as most organizations have increasingly shifted to a remote workforce. Tom further suggested that a surprisingly high number of USB key droppings are still used in attacks. Ben further suggested that cyber criminals are likely to continue to use social engineering type of attacks as human flaws, including curiosity is often the most persistent vulnerability in most organizations.
How Should Organizations Respond to an Attack?
Tom and Ben have provided insight concerning attack vectors as well as advice pertaining to how ransomware attacks are likely to evolve. Now let’s get their advice on how an organization should respond to a ransomware attack. Tom’s perspective is to encourage host or zone isolation to ensure the malware spread is stopped as quickly as possible and does not infect critical systems in the environment. He further suggested that organizations should gather as much data as possible prior to system isolation to understand how the malware is behaving on the system and how it may be communicating to a command-and-control system. Tom further suggested that once isolated, the cyber-criminal could change drastically his strategy, if it detects it can no longer communicate. It could even issue a self-destruct to destroy any traces of itself to prevent detection.
Ben further stated that ensuring you have a solid logging structure with backups is vital. This way, if there is a full-scale ransomware compromise and your data is destroyed, all systems can be at least restored, and data returned up to the point in time of the attack. Ben also suggested that “prior to implementing controls and procedures to help prevent or mitigate a firm’s risk of a ransomware attack, the firm should first know what data it collects, where the data resides, and who has access to the data.”
How Can Organization’s Protect Themselves More Effectively
We asked Ben and Tom which two or three actions they advise their clients to take to defend against a ransomware attack. Tom reiterated, "first, you need to have a solid game plan for system or network isolation. By implementing a Zero-Trust network design or segmenting the network with high value assets segmented properly, organizations will at least have an opportunity to limit the damage of an attack if the worst-case scenario occurs.”
Next is to have a solid incident response plan and ensure it is tested and practiced annually. Adding this capability to an organization will ensure SOC personnel has a clear plan to address the threat as quickly and thoroughly as possible. Tom explained that a dependable incident response plan should have a communication tree and a forensics plan for collecting and storing evidence.
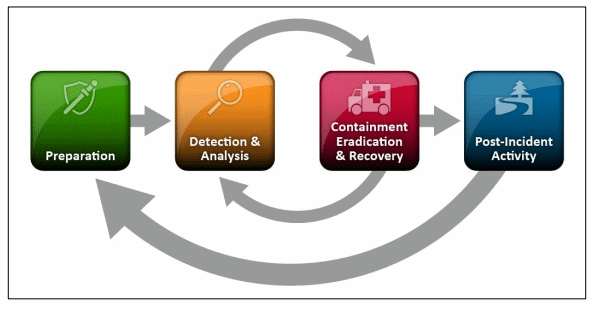
Figure 2 - NIST Incident Response Framework
Lastly, both Ben and Tom agree that companies should NOT pay the ransom. They stated that legislation and petitions are gaining support to stop organizations from paying ransom by making such payments criminally punishable. Many cyber threat intelligence experts like Ben and Tom suggest that paying the ransom will only exacerbate the global problem of cybercrime as ransom payments are certain to fund future attacks. In addition, Ben suggests “the FBI recommends not to pay ransom in response to a ransomware attack because it feeds the cybercrime industry. Furthermore, “Paying a ransom does not always guarantee that you will receive your data back or prevent future attacks.”
How Should Organizations Invest in Security Technology?
Throughout the interview, we asked Ben and Tom various questions about strategies companies can take or what types of tools can be used to best defend against ransomware. Ultimately, many of their answers boiled down to the same vector that continues to be exploited repeatedly; the people remain the weakest link. That said, security technology is always improving and both Tom and Ben recommend the best tools to both prevent and react to ransomware attacks.
Certainly, some tools are better than others, and there are some trends worth noting, but one common theme we continue to see and are constantly being exploited is the human element. As a society, we have made strides towards strengthening things like authentication and authorization to focus in on ensuring the intended users are logged in. Unfortunately, much of what we see with ransomware happens after the user is authenticated. Until a solid plan can be implemented to strengthen the castle's outer walls and the inner chambers that protect our sensitive treasures, society will continuously be plagued with Ransomware.
Ransomware as a Service (RaaS) Breakdown
Lastly, another common theme from the interview with Tom and Ben is Ransomware-as-a-service (RaaS) which we wrote extensively about in our blog post, The Emergence of Ransomware-As-A-Service. With threat actors now offering their ransomware packages online as a service, it has become increasingly easy to execute a ransomware attack. RaaS operations, such as REvil and Conti, have made their malware packages available on the dark web for a fee. Affiliates buy the RaaS kits and deploy them in company environments. Like legitimate SaaS offerings, RaaS may even include customer service support, bundled offers, and user forums.
Tom and Ben both agreed that the majority of attacks over the past 2 years or so were the result of criminals with little computer knowledge buying malware packages online and deploying advanced attacks. Attackers no longer need to spend as much time or money building an exploit and planning a high-level ransomware attack. This new RaaS trend has encouraged “script kiddies” or users with little computer knowledge to understand who is likely to fall for a phishing attack and who would likely pay a ransom with their data was encrypted. The success of RaaS comes from the lack of liability and the ease to monetize it quickly.
Conclusion and Key Takeaways
Tom and Ben wanted to leave us with three critical suggestions concerning how they help our clients here at Hitachi Systems Security protect their networks and data from all cyber-attacks.
Finally, we asked Tom and Ben what they would say to aspiring Cyber Threat Intelligence Experts in order to make them marketable in this environment. Both our experts suggested that while credentials like those listed below are still noticed by many organizations in order for an analyst or expert to show potential employers that they have a foundational level of IT security knowledge they are not the most critical element to building a successful career in cyber threat intelligence.
Some of the important cybersecurity certifications:
What is critical is showing a passion to continue to improve one’s knowledge by understanding what cybercriminal trends could affect you, how new malware strains behave, what new security technology is available and how organizations should manage risk cost effectively. They both added, “it is 100% certain that the threat landscape will look very different as malware, attack vectors, IT environments and security technology will all be almost unrecognizable 2 or 3 years from now.”
As we conclude our interview with Tom and Ben, we want to thank them for their time and invaluable insights. We will, no doubt be back to this forum with another compelling threat intelligence topic in the very near future.