
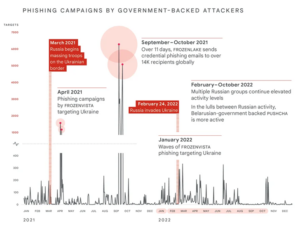
As we observe the solemn anniversary of the war on Ukraine, it’s clear that cyberattacks have comprised a significant part of Russia's armory. Cyberattacks against Ukraine surged by 250% in 2022 compared to the previous two years. Russia’s aggressive and multi-pronged cyber warfare strategy involves targeting the Ukrainian government, military entities, critical infrastructure, and the utilities, public services, and media sectors.
Multiple wiper strains – including WhisperGate, HermeticWiper, IsaacWiper, CaddyWiper, Industroyer2, and SDelete have been deployed against Ukrainian networks since the start of the war. Meanwhile, phishing attacks aimed at NATO countries spiked by 300% over the same period. Many of these attacks were driven by a Belarusian government-backed gang known as PUSHCHA (aka Ghostwriter or UNC1151,) that's known to be aligned with Russia.
The effects of the war on the dynamics among Eastern European cybercriminal groups make for an interesting study. Various hacking gangs and ransomware syndicates are taking sides to further their agendas. We’ve also seen a blurring of the lines between financially motivated attackers and state-sponsored actors. For instance, UAC-0098, a threat actor known for delivering the IcedID malware, has been observed repurposing its techniques to target Ukraine through a string of ransomware attacks.
Some members of UAC-0098 are former members of the now-defunct Conti cybercrime gang. TrickBot, which was absorbed into the Conti operation last year before the latter's demise, has now systematically targeted.
The ubiquity of Russian cyberattacks isn’t surprising when we consider recent political efforts to strengthen the country’s intelligence services and bolster their operational agility. These entities include:
FSB is the country’s primary domestic security agency and reports directly to Russia’s President. It oversees internal security and counterintelligence. In recent years, FSB’s remit has been expanded to include foreign intelligence collection and offensive cyber operations. It's believed that FSB augments its staff with criminal and civilian hackers. Cyber analysts have dubbed FSB hackers Berserk Bear, Energetic Bear, Gamaredon, TeamSpy, Dragonfly, Havex, Crouching Yeti, and Koala.
SVR is Russia’s primary civilian foreign intelligence agency tasked with gathering foreign intelligence through human and electronic signals and cyber methods. It uses advanced technical skills to breach networks and maintain access within them. Cyber experts refer to SVR hackers as APT 29, Cozy Bear, and the Dukes.
GRU is Russia’s most significant military intelligence agency. GRU cyber units operate multiple research institutes that focus on developing hacking tools and malware. Cyber analysts refer to these units as APT 28, Fancy Bear, Voodoo Bear, Sandworm, and Tsar Team.
The Internet Research Agency is a private group known to support the Russian government. It undertakes pro-Russia online influence and disinformation operations through social media channels and is known to impersonate domestic activists and other individuals as part of these efforts.
Despite the scope and sophistication of Russia’s cyber warfare operations, their impact hasn’t been as devastating on Ukraine as was initially expected.
This may be attributed to advances in defense technologies and the cyber-resilience of Ukraine. While the country hasn’t been able to seal its systems from Russian penetration completely, it’s adopted robust remediation and recovery tactics, such as backing up its files in overseas servers.
Ukraine was well-prepared because it’s been hardening its environment and strengthening its defenses for years. The country had been the target of substantial attacks from Russia well before the war broke out. These include strikes against the power grid in 2015 and 2016 and a 2017 virus aimed at Ukrainian businesses.
While it’s clear that cybercrime will continue to play an integral role in future armed conflicts, the rest of the world is taking steps to disrupt and deter it:
The scope of cyber sanctions and regulations is now broadening to include terrestrial and space networks. On March 2, 2023, the White House released a national cybersecurity strategy, identifying Russian and Chinese hackers as major threats to these infrastructures. In a statement, the White House said, “We face a complex threat environment, with state and non-state actors developing and executing novel campaigns to threaten our interests.”
As nations’ powers continue to grow, we’ll likely see more clashes in cyberspace than we have in the past. Diverse systems will be affected, and larger populations and areas will be subjected to more brazen tactics. When it comes to cyber warfare, everyone is vulnerable because there are no ground rules.
Mitigating the impact of future cyber warfare activities requires collaboration and intelligence sharing between governments, industry bodies, and businesses. Importantly, it will require getting the correct information to the right groups at the right time.
For their part, organizations need to be proactive about minimizing risk and preparing to respond if (or when) the worst happens. This should include the following: