Welcome to Part 4 in our 4-Part series on Cyber hygiene and what we at Hitachi Systems Security consider the three pillars of a quality Cyber hygiene program. In this last post of the series, we are going to discuss Incident Response and the growing focus organizations and the IT security industry have on IR and cyber resiliency. First let’s define the two terms so we can create some separation as we dig into discussing best practices around incident response. Incident response or IR is a set of information security policies and procedures that you can use to identify, contain, and eliminate cyberattacks. The goal of incident response is to enable an organization to quickly detect and halt attacks, minimizing damage and preventing future attacks of the same type.
Cyber Resiliency is the ability to anticipate, withstand, recover from, and adapt to adverse conditions, stresses, attacks, or compromises on systems that use or are enabled by cyber resources. Cyber resiliency is intended to enable mission or business objectives that depend on cyber resources to be achieved in a contested cyber environment. That definition is straight from NIST and helps make the point that IR is identifying, containing, and eliminating attacks while resiliency is the ability to minimize the time the attack stops business operations…to make the distinction between incident response and cyber resiliency clear.
We love the Ponemon surveys, particularly, The Cost of a Data Breach Report because it is the benchmark many of us in the IT security industry use to measure cybercrime and the average organization’s response to an attack. Now in its 17th year, the Cost of a Data Breach Report has become one of the leading benchmark reports in the cybersecurity industry. This report offers IT, risk management and security leaders a lens into dozens of factors that can increase or help mitigate the rising cost of data breaches.
Ponemon conducted 3,500 interviews, studied 537 real breaches across 17 industries and 17 countries. Data breach costs rose from $3.86 million to $4.24 million, the highest average total cost in the history of the report. The average total cost of a data breach increased by nearly 10% year over year, the largest
single year cost increase in the last seven years. The average cost was $1.07 million higher in breaches
where remote work was a factor in causing the breach, compared to those where remote work was not a factor. The average cost was $1.07 million higher in breaches where remote work was a factor in causing the breach, compared to those where remote work was not a factor. Remote work has become significant because the shift to work from home because of Covid-19 may be stickier that many IT security analysts are predicting.
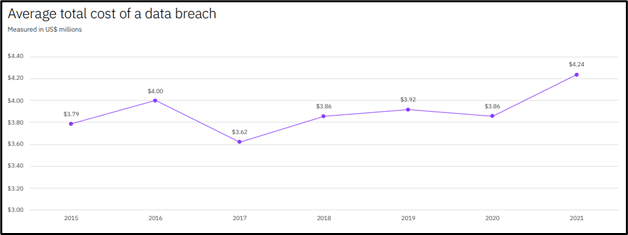
Lost business represented 38% of the overall average cost and increased slightly from $1.52 million in the 2020 study. Lost business costs included increased customer turnover, lost revenue due to system downtime and the increasing cost of acquiring new business due to diminished reputation. Customer PII was also the costliest record type, at $180 per lost or stolen record. The overall average cost per record in the 2021 study was $161, an increase from $146 per lost or stolen record in the 2020 report year.
Data breaches that took longer than 200 days to identify and contain cost on average $4.87 million, compared to $3.61 million for breaches that took less than 200 days. Overall, it took an average of 287 days to identify and contain a data breach, seven days longer than in the previous report. To put this in perspective, if a breach occurring on January 1 took 287 days to identify and contain, the breach wouldn’t be contained until October 14th. Think about that in the context of Log4j / Log4Shell with many organizations still trying to patch systems with the vulnerability. In many cases, systems may be compromised with criminals waiting for a time to make their next move.

According to the Ponemon Study, “The gap in average total cost between breaches at organizations with both IR teams and IR plan testing (IR capabilities), and organization with no IR team and no IR plan testing continued to grow. Breaches at organizations with IR capabilities cost an average of $3.25 million in 2021, compared to $3.32 million in 2020. The average total cost of a breach at organizations with no IR capabilities was $5.71 million in 2021, an increase from $5.09 million in 2020. The average total cost gap between IR capabilities vs. no IR capabilities was $2.46 million in 2021, representing a 54.9% difference.”
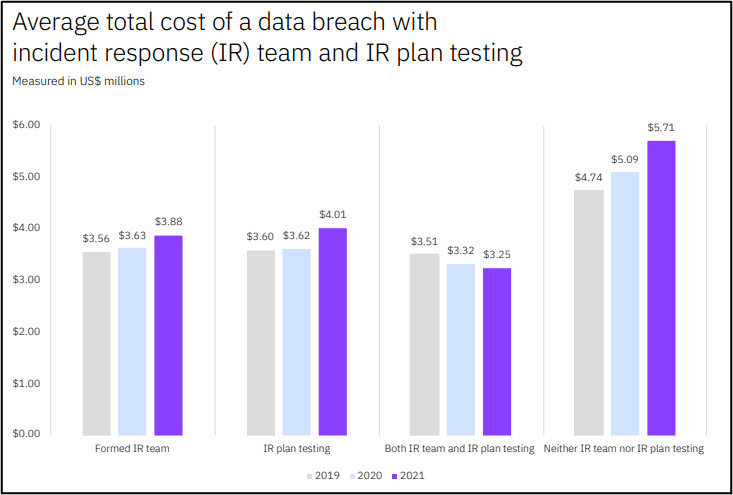
Ok, enough of the Ponemon report; I think we made the two points we hoped to make which are (1) Despite improving security technology and larger IT security teams, attacks are increasing and costing organizations more (2) Organizations that have a planned and tested IR plan in place lose less that have as much from a breach versus those organizations who do not have a tested IR capability in place.
An IRP is a set of documented procedures detailing the steps that should be taken in each phase of incident response. It should include guidelines for roles and responsibilities, communication plans, and standardized response protocols.
Within your IRP it is important to use clear language and define any ambiguous terms. One set of terms that are frequently confused is event, alert, and incident. When using these terms in your plan, it can help to restrict use as follows:
Gather a team of internal experts to put together the comprehensive data breach response plan. This plan should take into consideration the size of the business as well as the nature of the business. The response team should include forensics, legal, information security, information technology, operations, human resources, communications, investor relations, and management.
A security contact and resource manager are critical internal resources as the security contact will own the incident response plan and knowledge of the systems and resource manager will understand the business impact of any system downtime or other business issues.
Data forensics team. Organizations should consider hiring or outsourcing a digital forensic specialist that will be able to determine the scope and source of a breach. A digital forensic specialist will be able to gather forensic images from systems that were affected by the breach to process and analyze evidence for an internal investigation or law enforcement.
The specialists are often able to find the source of the breach, how the malware moved through the organization, and what damage the attack caused. Further, digital forensic specialists are also able to assist in updating incident response plans and revising policies to help prevent any future breaches.
Legal counsel. Companies should consider hiring legal teams with privacy and data security experience. These teams can advise your company on compliance legislation such as PCI-DSS and GDPR as well as federal and state laws that may affect their company in the case of a data breach.
Secure the organizational environment. Areas of the organization touched by the breach must be re-secured. Access codes, usernames, and passwords as well as any physical barriers should be changed and re-secured. Consult your forensic team and law enforcement to ensure the organizational environment has been made safe and secure.
Prevent any additional data loss. Ensure that all affected systems are quarantined, and the malware is isolated to known victim systems. That said, do not turn off any affected machines until your digital forensic expert informs you that it is okay to do so. Immediately update credentials and passwords of authorized personnel. This will prevent future data loss if the hacker has accessed credentials.
Legal requirements must be determined. Canada as well as all 50 States in the US, Puerto Rico, the District of Columbia, and the Virgin Islands have enacted laws that require notification of security breaches. Depending on the information involved there are different laws and regulations that apply. Check state and federal laws for specific requirements for your business.
Notify law enforcement. If a breach takes place notify your local law-enforcement agency immediately. Report that a breach has taken place and the potential for identity theft.
Electronic health information. Check the company to see if it's covered by health breach notification. If it is you must notify FTC, the FTC’s Health Breach Notification Rule explains all the information you will need to comply.
Also, check if the HIPAA Breach Notification Rule applies. If this rule applies you must notify the secretary of the US Department of Health and Human Services.
Notify Affected Businesses. Accounts may have been accessed and information may have been stolen. Information like credit card numbers and bank account numbers may have been compromised. If this is the case, do not leave the accounts open for further fraudulent activities; notify the institution and put safeguards in place for each account. Also, the institution will likely be able to monitor for fraud.
If the company collects and stores personal information that affects other businesses, notify them of the breach. If Social Security numbers have been taken, contact credit bureaus immediately. If the breach involves large groups, notify credit bureaus of the breach including those below.
Equifax: equifax.com 1-800-525-6285
Experian: Experian.com 1-800-397-3742
TransUnion: transunion.com 1-800-680-7289
Notify Individuals. The faster you notify individuals their information has been breached, the quicker the individual can take steps to ensure their information is not used in a fraudulent manner. Deciding who to notify is critical as many touchpoints are time sensitive. Criminals who have stolen Social Security numbers and names will be able to use that information to open new accounts and commit identity theft. If notified early victims can take proper steps to limit these activities.
Because this is the last post in our 4-part series on Cyber hygiene best practices, let’s circle back and revisit the recommendations and information we provided, which of course is just our perspective. We are suggesting that a quality vulnerability management program, a security posture assessment to understand where your level of risk is today, and a reliable incident response program will serve as the foundation of a quality Cyber hygiene program.
We understand that implementing programs like these are not simple for any organization, particularly those that are just starting to move up the security maturity curve. There are challenges with a lack of specialized people, implementing new processes, particularly with patching systems and integrating new technology. Our goal was to provide a blueprint that we have provided to organizations as a means to improve security defense.
Because we mentioned Cyber Resiliency in the top of the post and we will likely create a post on the topic soon let’s quote one more Ponemon Study on Cyber Resiliency. “Both the volume and severity of cybersecurity incidents increased or significantly increased in the past 12 months, according to 67% of respondents. Of the respondents surveyed, 51% sustained a data breach over the last 12 months and 46% experienced at least one ransomware attack over the past two years.”
Incident Response and Cyber Resiliency capabilities for organizations is critical because it is clear the security defenses of most organizations will be breached at some point. We certainly don’t want to fear monger, just make it clear that reacting to incidents properly with tested IR processes in place will limit the cost, damage, and time it takes to mitigate the attack.