Why Ransomware-as-a-Service (RaaS) is Exploding as a Cyber Threat
Ransomware-as-a-Service or RaaS can be purchased by any individual or group that wants to launch a cyberattack, and they can easily find a package to suit their needs for any target. In last year’s research by Cybersecurity Ventures, the documented non-state individuals, financially motivated groups, and in some cases, state groups starting services that provided neatly packaged ransomware that could be bought or leased by anyone with a hundred dollars or more. Later that year, that chatter on the dark net around RaaS increased and was being discussed by cybercriminals who were interested in committing corporate espionage to exfiltrate sensitive information, including intellectual property.
The research further suggests that the Ransomware- as-a-Service movement seemed to have been started by Russian cybercriminal groups APT 28/28 and FIN 7/11, as well as the Korean cybercriminal group Lazarus and its affiliates.
There are also several non-state groups capitalizing on RaaS, buying and selling for financial gain. The research notes that Chinese and Vietnamese groups are using RaaS as well but in a different way. They seem to be implementing the RaaS system as an element to hide their primary cybercrimes.
The industrialization of attacks has progressed from attackers using off-the-shelf tools, such as Cobalt Strike, to attackers being able to purchase access to networks and the payloads they deploy to them. This means that the impact of a successful ransomware and extortion attack remains the same regardless of the attacker’s skills.

Figure 1 - How the RaaS model enables ransomware attacks
With the ease of packing and distributing the malware on the dark net, the number of sales has increased dramatically. To illustrate, think about the astounding volume of attacks; Microsoft processes 24 trillion signals every 24 hours and has blocked billions of attacks in the last year alone. Microsoft Security tracks more than 35 unique ransomware families and 250 unique threat actors across observed nation-state, ransomware, and criminal activities.
Unlike the broad targeting and opportunistic approach of earlier ransomware infections, attackers behind these campaigns vary their attack patterns depending on their discoveries. For example, a security product that isn‘t configured to prevent tampering or a service that’s running as a highly privileged account like a domain admin. Attackers can use those weaknesses to elevate their privileges to steal even more valuable data, leading to a bigger payout for them. The more troubling issue for organizations is that the cybercriminals may lie in wait in their target environment once they’ve been paid. Attackers will stay on a network once they gain access and sometimes repeatedly monetize that access with additional attacks using different malware or ransomware payloads if they aren’t successfully evicted.
Defining the Ransomware-as-a-Service Business Model
In the past year or so, Ransomware-as-a-Service or again, RaaS has emerged as a business model in which developers sell or lease compact, easily deployable, and scalable malware toolkits to individuals and groups who want to stage cyberattacks. It’s promoted and sold on the dark web using the same marketing and sales tactics that legitimate businesses use on the regular web which include display ads, search engine optimization and more.
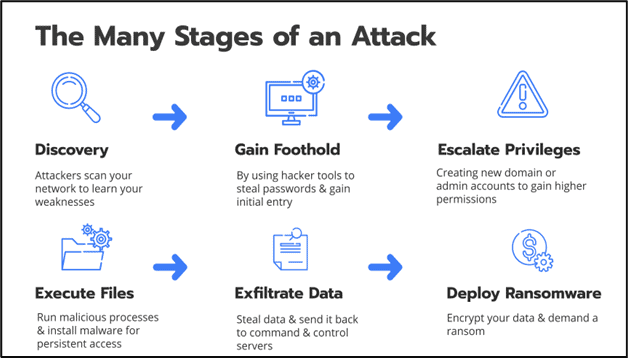
Figure 2 - The Stages of a Ransomware Attack
For example, if you were to enter the dark web, you’d find display ads in underground forums promoting RaaS kits with different price points and varying degrees of service; just like the ads you encounter on social media and elsewhere on the web. There are bundles, discounts, 24-hour support, user reviews, and all the other web marketing elements you might see employed by a Software-as-a-Service (SaaS) business.
There are four common RaaS revenue models:
The alarming part of the RaaS story so far is the ease in which launching a malware attack across the web has become for cyber criminals. We have seen literally thousands of RaaS attacks take advantage of business’s weak cyber security measures, including poor patch management, weak security technology management, and ineffective incident response efforts. The attackers easily encrypt the victim’s folders and other data locking them out of their own systems, databases, and other devices. Victims range from individual computer users to small businesses all the way up to large enterprises. Ransomware operators then demand money, mostly in the form of crypto currency, to decrypt the ransomed files.
Whether or not payments are made between the operator and the peddler, many organizations are left crippled or unable to continue operations altogether.
From Script Kiddies to RaaS (Ransomware-as-a-Service)
In just a couple of years we have seen RaaS grow to the point where there are now literally thousands of hacking and security programs on the dark web. These programs are written by fairly skilled programmers and hackers who often offer the malware for free to download and use. This can be a blessing to the user who wants to learn cybersecurity, however, it can spell trouble when a script kiddie tries to use them for hacking.
A script kiddie, or “skiddie,” is someone who lacks programming knowledge and uses existing software to launch an attack. Often a script kiddie will use these programs without even knowing how they work or what they do. For example, imagine a child gets their first computer. The child watches a movie about hacking and then downloads a copy of Kali Linux. They begin playing with the various programs while searching for online tutorials. At first, they may be perceived as nothing more than an internet troll due to their lack of experience and quickness to brag and boast. Sometimes they will even resort to cyberstalking or bullying.
The malware available to these folks now is far more damaging and sophisticated than before. Now, they can be quite remarkable at causing damage despite their lack of experience. Additionally, they can use social engineering techniques to manipulate users and steal data.
Ransomware Attacks a Business Every 11 Seconds
Ransomware continued its upward trajectory over the past year, and it’s expected to attack a business every 11 seconds this year, according to Cybersecurity Ventures. A lot of that has to do with the digitalization rush caused by the COVID-19 pandemic. While companies were innovating and overhauling their business models, cybercriminals were developing their own software to make it easier to hold your data hostage.
Cybersecurity Ventures saw a 195 percent growth in acceptance of RaaS by cybercriminal communities in 2020 and the trend is still growing exponentially. These cybercriminals have had an incredibly successful year, which is only going to motivate them to continue developing and making it easier every day for organizations to be compromised.
Last year, we saw a massive change in how ransomware campaigns were executed. Cybercriminals would infect the victim’s network with malware, and exfiltrate data before leaving behind a ransom note with threats to name-and-shame the victim organization in public forums.
This year, we will see more attacks that include an added step where hackers will leave residual malware in the system and re-enter the network whenever they choose to go back for additional data or request more ransom payments. Ransomware attacks have proven to be highly profitable for hackers and this has fueled the underground economy with a new business model and ecosystem.
Buying a Ransomware-as-a-Service kit or service package is as easy as buying any Software as a Service product, without the need for deployment and implementation.
RaaS malware and other tools can be purchased online and used directly on the target as a payload to execute the cyberattack. It’s so easy, almost 44 percent of the RaaS kits available on breach forums across the dark web are eventually launched against targets by buyers. RaaS is essentially a gift-wrapped cyberattack for anyone with a target and enough money to purchase the appropriate kit.
Conclusion
All human-operated ransomware campaigns as Microsoft categorizes RaaS, share common dependencies on security weaknesses that allow them to succeed. Attackers most commonly take advantage of an organization’s poor credential hygiene and legacy configurations or misconfigurations to find easy entry and privilege escalation points in an environment.
Without the ability to steal access to highly privileged accounts, attackers can’t move laterally, spread ransomware widely, access data to exfiltrate, or use tools like Group Policy in Windows to impact security settings. Disrupting common attack patterns by applying security controls also reduces alert fatigue in security SOCs by stopping the attackers before they get in. This can also prevent unexpected consequences of short-lived breaches, such as exfiltration of network topologies and configuration data changes that happen in the first few minutes of execution of some trojans.
Often, during reconnaissance, the attackers take note of security products in the environment and attempt to tamper with and disable these, sometimes using scripts or tools provided with RaaS purchase to try to disable multiple security products at once or use specific commands or techniques to disable or maneuver around the security technology.
This knowledge is key for SOCs responding to ransomware: prioritizing investigation of alerts or detections of tools like Cobalt Strike. Performing swift remediation actions and incident response (IR) procedures are critical for containing an attack before the ransomware deployment stage. Security teams will be challenged to defend against RaaS attacks in the coming years and of course we would love to help.