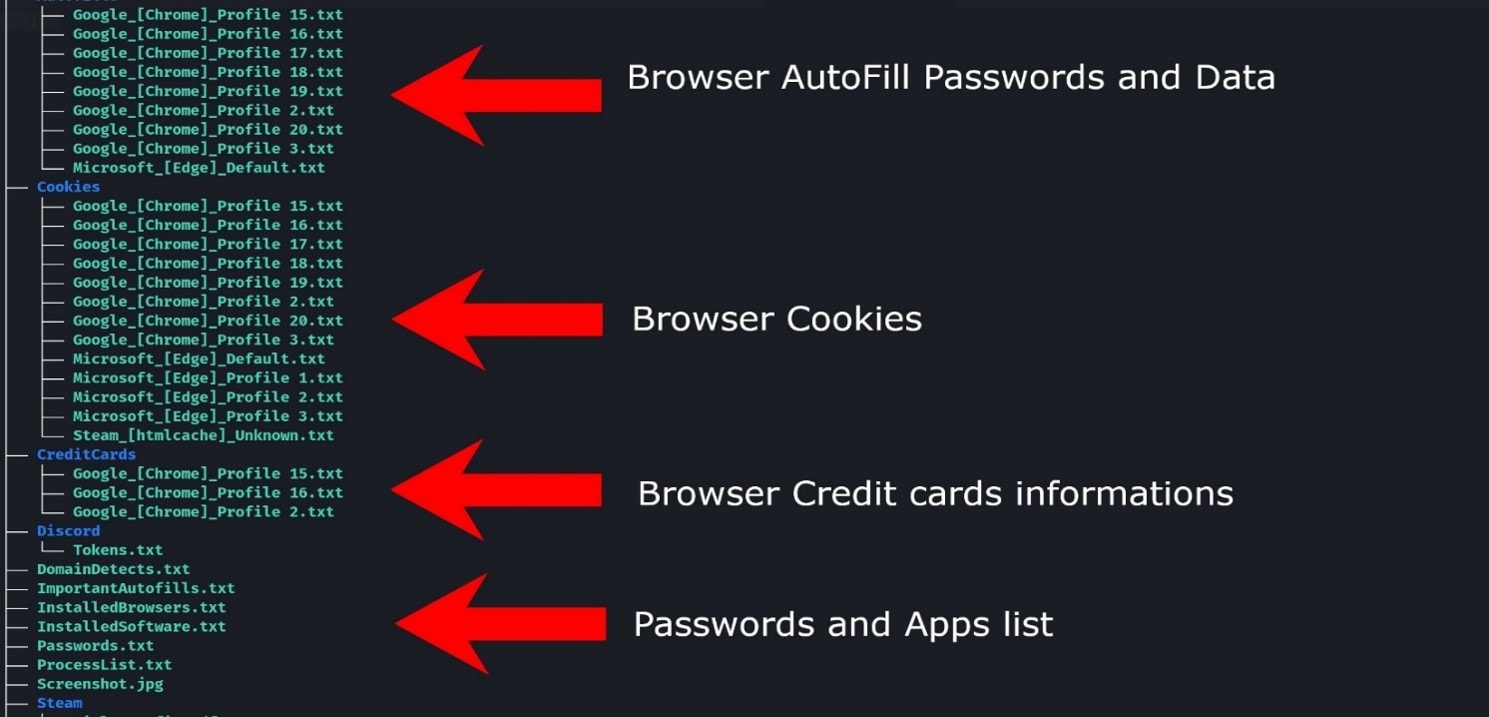
What information of yours is public? What about your firm? Your employees? Your vendors? Is your company compliant with industry standards? What are your hidden and open online weaknesses?
We empower your organization with the right cyber intelligence to keep your people, information and technology safe.
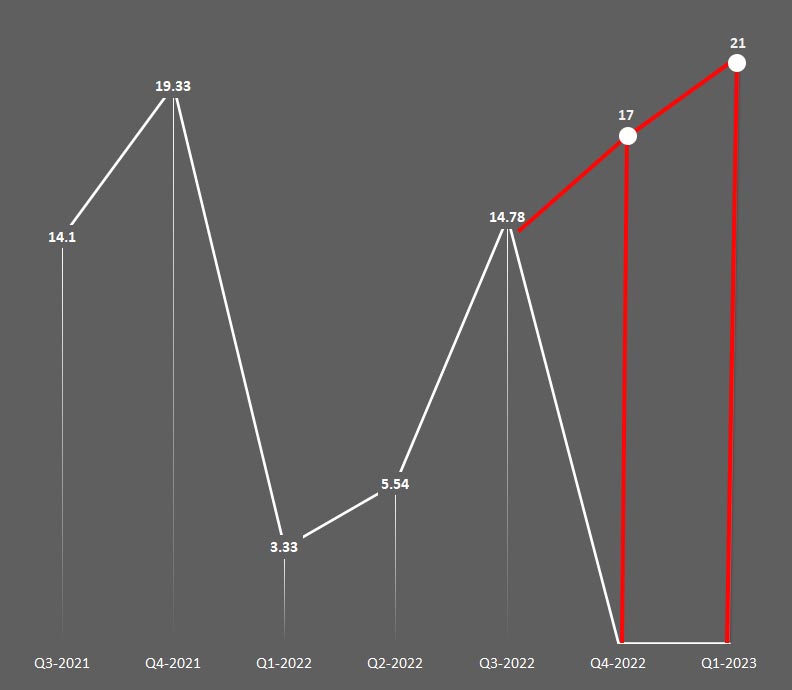
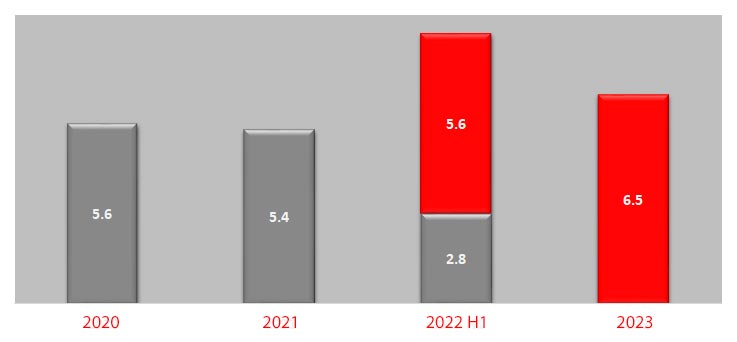
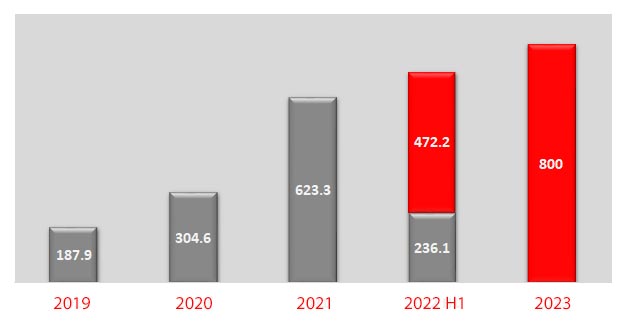
Without effective prevention measures in place, your organization may be vulnerable to ransomware attacks, which can result in data loss, downtime, and lost productivity.
Paying the ransom may not guarantee the return of the encrypted data, and encourages future ransomware attacks.
By implementing robust ransomware prevention measures, you can reduce the risk of becoming a victim of this type of attack and protect your valuable data and assets.