Cyber hygiene is a broad, critical topic for IT security and frankly it often has different definitions with even top IT security consulting firms. Moreover, their perspective of achieving good Cyber hygiene is different and can be somewhat nebulous and complicated as well. The goal of this 4-part blog post series is to provide you a clean definition of Cyber hygiene and what we at Hitachi Systems Security believe are the three critical pillars critical to achieving a good Cyber hygiene program.
Before we get in to the three critical pillars let’s address Cyber hygiene itself to create a baseline of understanding of the term. In many ways Cyber hygiene is synonymous with an organization’s security posture; I hope we can agree on that. I’m suggesting that if an organization has good security posture and scores well across a NIST, ISO, or CIS 20 framework, their Cyber hygiene will be excellent as well.
However, strengthening an organization’s cyber security posture is complex; and dealing with the challenge of technology, as many organizations do, isn’t enough. The process should start with implementing fundamental cyber security practices, which we believe is the foundation of Cyber hygiene. Just like personal hygiene, Cyber hygiene’s objective is to start with basic actions that are most likely to support good health. Despite the popular belief that cyber hygiene is exclusively the IT department’s job; however, Cyber hygiene should involve all departments and be part of the organization’s culture.
In a recent Forrester Consulting survey, 94% of security and business executives found that their organization have experienced a "business-impacting" cyberattack or compromise in the past year. Business-impacting according to the survey is defined as an attack that resulted in the loss of customers, employees, or confidential data (PII). Further, any interruption of day-to-day operations, a ransomware payout, or other financial loss or theft of intellectual property would be included.
That's a very powerful number, especially when talking to the executives in the C-suite," says Forrester analyst Wenzler. "Security pros can now go to top management and offer proof that cyberattacks will impact their businesses and that they have to do something about it."

Meanwhile, threats go beyond technology and external hackers. Human fallibility is often the root cause of breaches. Cyber-attackers are no longer breaking in—they’re logging in using weak, default, or compromised passwords. Once they compromise security measures, adversaries are able to inflict real damage by moving laterally across the network, seeking privileged access to critical infrastructure and sensitive, potentially valuable data.
The IT department alone cannot mitigate identity-based attacks. Ultimately, it’s a responsibility shared by all employees from C-suite to summer interns, as well as partners and contractors. “If you look at the most major ransomware attacks that have occurred, basic cyber hygiene could have prevented the vast majority of them, so, killing their ability to move laterally,” Matthew Swenson, chief of the Department of Homeland Security’s (DHS) Cyber Crime Unit at Homeland Security Investigations (HSI), said during a recent webinar. “Heavy network segmentation, network security monitoring, zero trust models, multi-factor authentication, all those types of things.”
“I think you start from the basic cyber hygiene, work your way up, and as you start to prevent just those basic things and get more and more secure, I think you do end up preventing the vast majority of these types of attacks,” he added.
In the new ‘digital normal’, traditional perimeter or layered technology defense is no match against the influx of cyber threats. Many businesses do not have a clear view of their growing attack surface, and often a poor understanding of their overall risk. Security analysts, consultants and we at Hitachi Systems Security see several new developments which will impact the cyber landscape this year and beyond.
The pandemic that dramatically increased the number of remote workers coupled with legacy security set-up has expanded most organization’s attack surface. We have seen that cybercriminals have evolved their attack tactics to exploit remote workers who are the easiest and most vulnerable entry points into organizations through even the most rudimentary phishing attacks.
This trend will continue given that many organizations continue to use legacy approach and security architecture, for example, VPNs and RDP, as enablers for remote working. With zero-trust framework still not widely adopted, an increase in attacks is expected by nearly the entire security community. Of course, the result is operational disruption, brand damage and financial loss.
Cybercriminals have been escalated their ransomware attacks using three-phased approach where they would infiltrate the network, exfiltrate and encrypt data, and demand ransom while threatening to ‘name-and-shame’ victims on public sites.
Ransomware-as-a-service (RaaS) has seen a drastic increase where low-skilled hackers are able to rent ransomware code, customize it, and deploy in real-world attacks, usually to collect lucrative ransoms from Government institutions, schools, and smaller organizations.
Cyber hygiene must become engrained in an organization’s daily routine to be effective. For example, this goes beyond enforcing password policies as some suggest, and requires organizations to take a holistic approach to improving security across the entire organization. When applied correctly, cyber hygiene can help protect against the most common cyber threats.
I’m absolutely certain that experts all over the cybersecurity community could argue what three elements are most critical to improving an organizations overall security posture and Cyber hygiene. That said, we’ve put our heads together here at Hitachi Systems Security to introduce our three pillars.
Vulnerability management exists for the purpose of identifying and remediating vulnerabilities in systems quickly before they are exploited. Vulnerabilities, which are essentially weaknesses within software that can lead to a system or network that can be exploited by attackers. These vulnerabilities must be identified, assessed, and patched regularly to ensure ongoing security. In order to create and maintain a strong security posture, business owners and security officers must be keenly aware of the vulnerabilities on their systems, as well as the process by which they can be quickly patched. If vulnerabilities are not identified or remediated, companies leave themselves open to attacks.
According to a recent Verizon’s Data Breach Investigation Report, “98% of security incidents and 88% of data breaches continue to occur within one of nine patterns.” Understanding and taking steps to guard against the common patterns and approaches attackers use to infect your system will greatly increase the security posture of your company. The most important way to do this is to frequently scan for known vulnerabilities. These common weaknesses often have patches available from the software manufacturer that will eliminate the vulnerability.
Cybersecurity frameworks provide a blueprint to identifying, prioritizing, and creating an ongoing plan for organizations to improve their posture over time with audits and scoring. Let’s start with the CIS 20; it is by far the easiest to understand, use and score with far few items to assess than both the NIST and ISO assessments.
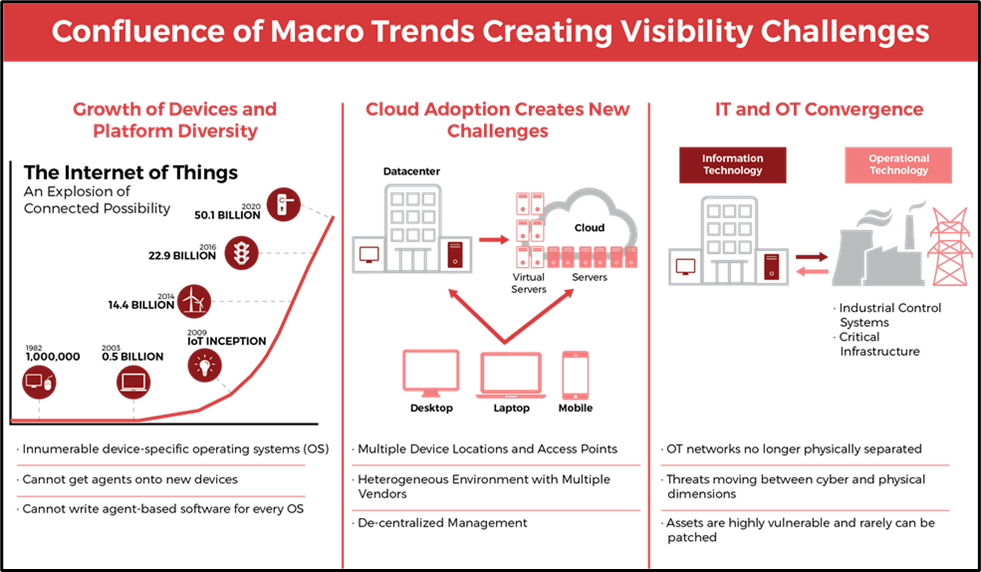
The Center for Internet Security (CIS) Top 20 Critical Security Controls (previously known as the SANS Top 20 Critical Security Controls), is a prioritized set of best practices created to stop the most pervasive and dangerous threats of today. It was developed by leading security experts from around the world and is refined and validated every year. One of the keys here is addressing the threats of today. We provided a chart below that identifies several of the daunting challenges IT security teams will face over the next several years.
Getting started with any one of the frameworks is fairly straight forward. All of the frameworks essentially start by asking yourself these questions to assess how well the organization is managing cyber risk:
We found the Forrester findings to be aligned with what we see across businesses and from industry to industry. What we mean is that if an organization has put themselves through a security posture assessment like CIS, ISO, or NIST, that exercise will force them to evaluate high-value systems, their security hygiene processes, and their path to more effective security defense…at a minimum.
What seems to be evident in the Forrester survey is that the majority of organizations still have not put themselves through a valid assessment.
Almost a third of US businesses were breached last year according to an HSB survey of 403 senior executives in the U.S., conducted by Zogby Analytics. HSB, a leading provider of cyber insurance for businesses and consumers suggested that with an increasing amount of both personal and business data available online, the risk of exposure will increase in proportion. The financial impact of a data breach reported in the survey was considerable as well: 27 percent of the victim organizations spent between $5,000 and $50,000 to respond to the breach and 30 percent spent between $50,000 and $100,000.
The survey also revealed that 51% of the executives thought their IT security staff “lacked a plan” to deal with the breach, 41% didn’t have the required knowledge to handle the breach adequately and 38% lacked the resources.
Ponemon Institute shocked the cybersecurity industry a number of years ago when they published a survey of 567 executives, of whom 43% suggested they had experienced a data breach or perhaps a security incident, if you examine the details in the survey, in the prior 12 months. While security incidents and data breaches are apples and oranges, the trend and any back of the napkin analysis paints a fairly grim picture – the number of organizations that are damaged significantly from a cyber-attack is growing at a rapid pace.
The Ponemon survey also revealed that 68% of respondents felt unprepared to respond to a data breach and 30% of respondents felt their data breach response plan was flat-out ineffective. Clearly, the response to security incidents has not improved in proportion to the sophistication of the attacks as well as the number of attacks.
Conclusion
Ultimately, organizations should keep in mind that maintaining cyber hygiene is a business problem, not an IT problem. As such, organizations should implement the recommendations listed above in policies, plans, processes, and procedures. A gradual improvement in cyber hygiene can go a long way toward keeping an organization immune from security infections and minimizing the risk of falling victim to a cyber-attack.
A significant number of organizations and security leaders see Cyber hygiene as somewhat theoretical rather than something measurable that their organization should strive to identify and set goals to reduce. Most professionals in the IT security or cybersecurity industry understand it is difficult to set a value to systems, litigation costs, brand damage costs, ransomware costs, data loss costs, compliance penalties and so many other difficult to estimate variables.
Thus, Cyber hygiene best practices are often not implemented or measured. We are suggesting that a quality vulnerability management program, a security posture assessment to understand where your level of risk is today, and a reliable incident response program will serve as the foundation of a quality Cyber hygiene program. In the next 3 blogs posts we’ll tie all this together to discuss our thinking, why you should focus on these 3, and how to implement them.