Protect Your Organization from Ransomware with a 4-Step Approach
In putting together this blog post on defending against this new wave of ransomware attacks we reviewed research from a variety of surveys including the Verizon Data Breach Report, the Cybersecurity Insiders Survey, the Ponemon Survey Data, a survey conducted by HelpSystems in conjunction with Cybersecurity Insiders.
Key findings in the benchmark cybersecurity surveys include:
Phishing Attacks are the Common Vector for Ransomware
Last year during a 12-month period starting in Q2 ransomware attacks increased over 365% against businesses, however, only 12% against consumers. The transition for larger extortion payouts has been increasing over the last several years.
The malware is most often delivered through phishing e-mails and now more commonly spear-phishing emails. As we know, the ransomware once downloaded on the system encrypts hard drives or other parts of the system that makes data difficult or impossible to access.
While there are countless types of ransomware strains and families, 3 families of the malware have done a significant amount of the damage: Dharma, Ryuk and GandCrab.
Dharma Ransomware
Still, it currently has three separate systems in circulation, each of which has several variants that go under different names. The old system in this family is called Crysis. That was first released in February 2016. Dharma is the second in the series, released in July 2018, and Phobos brings up the rear, releasing in September 2019.
The three family members are difficult to distinguish because they share a lot of code. Typically, anti-malware systems can’t distinguish between them, often flagging Dharma as Crysis. The situation is complicated further by a large number of variants of each. What makes Dharma so successful is that it spreads by targeting internet-facing ports and remote desktops. Microsoft created the Remote Desktop Protocol (RDP) and it is integrated into Windows. This means that Dharma was specifically designed to attack computers that have the Windows operating system.
As opposed to most ransomware attacks that leverage phishing attacks, Dharma can gain access to networks without even having to get a victim to click a link or download a malicious file from a phishing email. The malware is manually delivered by attackers who exploit Remote Desktop Protocol (RDP) services via TCP port 3389 and brute force the password to gain access to a computer.
Ryuk Ransomware
A variant of the older Hermes ransomware, Ryuk tops the list of the most dangerous ransomware attacks. In last year’s CrowdStrike Global Threat Report, Ryuk accounts for three of the top 10 largest ransom demands of the year: USD $5.3 million, $9.9 million, and $12.5 million. Ryuk has successfully attacked industries and companies around the globe. Hackers call the practice of targeting large companies “big game hunting” (BGH).
A Russian cybercriminal group known as WIZARD SPIDER is believed to operate Ryuk ransomware. UNC1878, an Eastern European threat actor, has been behind some healthcare-specific attacks. The deployment of this ransomware is not direct; hackers download other malware onto a computer first.
When Ryuk infects a system, it first shuts down 180 services and 40 processes. These services and processes could prevent Ryuk from doing its work, or they are needed to facilitate the attack. It is estimated that Ryuk earned it’s the Russians more than $3.7 million in its first four months.
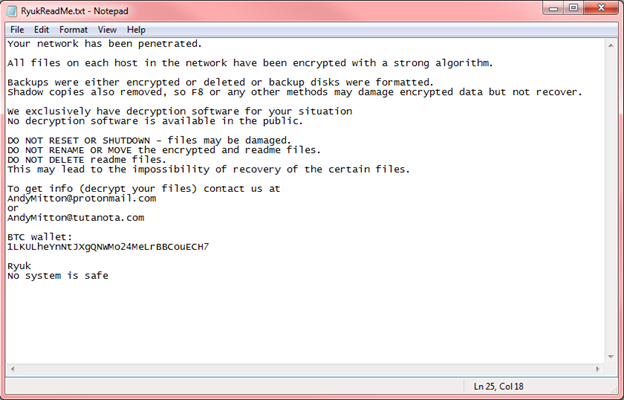
The hackers leave ransom notes in the system as RyukReadMe.txt and UNIQUE_ID_DO_NOT_REMOVE.txt that read something like the following image.
GandCrab Ransomware
Similar to most ransomware strains, the GandCrab now offers ransomware-as-a-service to interested criminals on the dark web and encrypts the data on a system however, GandCrab far eclipsed the success of competing ransomware affiliate programs largely because its authors worked to update the malware so that it could evade antivirus and other security defenses.
GandCrab is distributed via multiple spreading vectors, which include spam emails, exploit kits and other affiliated malware campaigns. GrandSoft and RIG are the two most commonly used exploit kits for distributing GandCrab along with the high number of malicious spam emails. These spam emails trick users into opening the file contained inside the attached ZIP archive, which is generally a script that downloads the GandCrab ransomware and executes it.
Like Dharma, when free decryption tools were released to combat GandCrab its developers released new versions. The group behind GandCrab suggested that they earned over $2 billion but have now ceased operations suggesting their first of its kind ransomware-as-a-service model has made them comfortable.
A decryption tool for the most recent version of GandCrab is available from the awesome group No More Ransom.
The 4 Step Solution to Protecting Against Ransomware Attacks
Because IT security, incident response and cybersecurity organizations in general have investigated so many ransomware attacks over the past several years, we are all getting a sense of how to defend more effectively. That said, the team at Hitachi Systems Security has taken our philosophy and blueprint for defending and responding to a ransomware attack. The team has leveraged their deep understanding of how ransomware infiltrates a system, spreads throughout a network and uses locks data and system functions to attack in order to create the following four steps that organizations should take to defend against an attack.
4 Steps Organizations Should Take to Defend and Respond to Ransomware Attacks
In cyber or IT security we typically refer to an attack as having “Land and Expand” strategy. Meaning the cyber-criminal must get the malware onto a system first, then, after they “Land,” the attacker must move the malware to other systems by escalating credentials or some other means to “Expand” their attack and find the most lucrative victims.
Based on the attack strategy Let’s walk through how to execute the 4 steps and how they can help close the gaps that cyber-criminals use to steal billions from their victims.
Prevention through Social Engineering Training and Effective Patch Management
The prevention strategy is aimed at hardening systems or targets against attacks. Systems are reinforced against phishing attacks, RDP/Remote Access attacks, and other attacks a best practice approach to eliminating vulnerabilities. Prevention is about implementing:
Isolate Infected Systems Immediately and Minimize Privileges
As we suggested at the beginning of the section, attackers leverage the “land and expand” strategy to exploit one system and move through the organization until they find sensitive data or whatever information they hope to find. They use lateral movement to pivot from the first system to other systems that hold the data that they are targeting. This privilege escalation is executed by the attacker using vulnerabilities in systems to methodically obtain additional privileges as they move through the organization’s environment to ultimately compromise higher value targets.
To prevent an escalation of the attack or lateral movement of the malware from one system to another you must first take your system off the network. You don’t necessarily need to shut down the system, however it should be isolated.
Also, administrators should use separate accounts; one for day-to-day business use including web browsing and emails and a privileged administrator account that should only be used on separate administration devices. This reduces the risk of an infected device being used for administrative purposes.
Finally, administrator accounts should be prevented from browsing the web and accessing emails, and only be used when a task requires elevated permissions. The principle of 'least privilege' should be implemented wherever possible. Users should only have the privileges necessary to do their job.
Backup Systems and Verify the Malware has been Eliminated
In a Vanson Bourne survey of 500 cybersecurity decision makers sponsored by SentinelOne last year, 48 percent of organizations said they had experienced at least one ransomware attack in the last year, with the average organization experiencing 6 attacks with the recovery time over 33 hours on average.
Thus, how do you recover quickly from a ransomware attack? Let’ discuss two critical ways:
Improve Security Controls to Prevent Attacks
According to Wikipedia security controls are “Security controls are safeguards or countermeasures to avoid, detect, counteract, or minimize security risks to physical property, information, computer systems, or other assets.” Good definition. Let’s look at a one example:
Conclusion
Ransomware is the most prevalent threat facing organizations of different sizes and in nearly every industry. In fact, it is estimated that the damages done by ransomware attacks cost more than $20 billion globally in 2021 and this number is expected to reach $265 billion by 2031. In ransomware cases investigated over the past year, 95% of cybersecurity issues can be traced to human error and 43% of all breaches are threats from within an organization, whether malicious or accidental, according to The Global Risks Report published by the World Economic Forum (clicking this link will download the 117 page report). And, as we said, in the vast majority of cases, a single device will likely be the starting point of a company-wide attack.
Cybercriminals are constantly creating and testing new vectors and variants of ransomware including ransomware-as-a-service. Because of this, the number and complexity of the attacks has risen dramatically. RDP (Remote Desktop Protocol), Phishing and software vulnerabilities are allowing attackers fairly easy access to systems. We hope this blog post on the 4 keys to protecting and recovering from a ransomware attack will help your organization.