In part 1 of this 4-part series on Digital Transformation (DX) we discussed what DX is, the benefits, the 4 types of digital transformation and why organizations struggle to implement new technologies. In part 2 we discussed the manufacturing industry and its opportunities and challenges as it evolves through it evolves through the digital transformation. In part 3 we discussed the financial industry, which likely has the most opportunities and risks as banks, hedge funds, exchanges, and broker dealers among others navigate through DX. Further, security is key as financial institutions have the most to lose if they are breached.
In part 4, our final blog post of the Digital Transformation blog series we are going to focus on the growing attack surface IT security organizations are having to protect because of the digital transformation. We are going to introduce you to a variety of new terms and acronyms that, we promise you’ll hear almost at nauseum going forward.
Let’s start with Gartner who suggests, “security and risk management leaders must address seven top trends to protect the ever-expanding digital footprint of modern organizations against new and emerging threats now and beyond.
“Organizations worldwide are facing sophisticated ransomware, attacks on the digital supply chain and deeply embedded vulnerabilities,” said Peter Firstbrook, research vice president at Gartner. “The pandemic accelerated hybrid work and the shift to the cloud, challenging CISOs to secure an increasingly distributed enterprise – all while dealing with a shortage of skilled security staff.”
Gartner further suggests that these challenges lend themselves to three overarching trends impacting cybersecurity practices:
Ok, we know what you are thinking, “these are pretty broad overarching trends, and they aren’t any different than the trend that we’ve been dealing with since the start of the cyber industry.” We agree, so let’s dig in the attack surface issue and how we at Hitachi Systems Security provide practical solutions to our clients to protect themselves from attacks in this new environment.
Gartner is good at a lot of things but coining terms and creating acronyms is right up there in their core competency. Enterprise attack surfaces are expanding. Risks associated with the use of cyber-physical systems and IoT, open-source code, cloud applications, complex digital supply chains, social media and more have brought organizations’ exposed surfaces outside of a set of controllable assets.
IoT or the Internet of Things is the major contributing factor to the digital transformation; in recent years is the explosive growth of devices connected and controlled by the Internet. The wide range of applications for IoT technology mean that the specifics can be very different from one device to the next but there are basic characteristics shared by most. IoT creates opportunities for more direct integration of the physical world into computer-based systems, resulting in efficiency improvements, economic benefits, and most importantly access to data and systems from anywhere at any time.
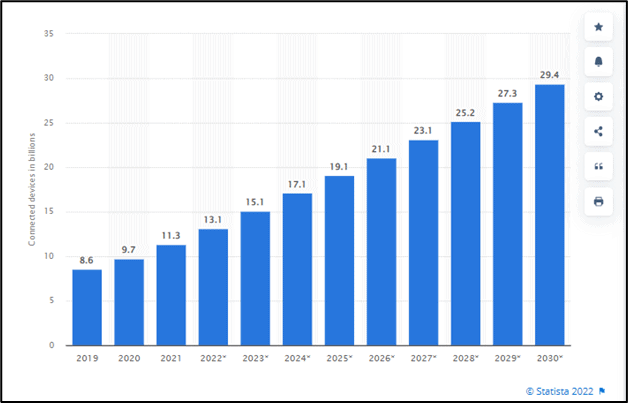
Figure 1 - Number of Internet of Things (IoT) connected devices worldwide from 2019 to 2030
The issues IT security organizations are facing is trying to control access, monitor systems, protect sensitive data, secure their new cloud infrastructure, and prevent employees from being duped by the deluge of social engineering attacks that are far and away the attack vector used most.
Organizations must look beyond traditional approaches to security monitoring, detection, and response to manage a wider set of security exposures. Gartner suggests, digital risk protection services (DRPS), external attack surface management (EASM) technologies and cyber asset attack surface management (CAASM) will support CISOs in visualizing internal and external business systems, automating the discovery of security coverage gaps. This simply means that heads of security need to leverage new expertise (people), improved vulnerability identification (processes) and embrace leading edge security products (technology.)
The attack surface is the number of all possible points, or attack vectors, where an unauthorized user can access a system and extract data
Simply, the IoT system architecture consists of three tiers: Tier 1: Devices, Tier 2: the Network, and Tier 3: the Cloud. Let’s end this section with a very clear definition of an attack surface then we’ll discuss how to protect it in the next several sections. The attack surface is the number of all possible points, or attack vectors, where an unauthorized user can access a system and extract data. The smaller the attack surface, the easier it is to protect. The digital attack surface area encompasses all the hardware and software that connect to an organization’s network. These include applications, code, ports, servers, and websites, as well as shadow IT, which sees users bypass IT to use unauthorized applications or devices.
It is more important than ever to understand your attack surface because there is NO WAY you can protect every asset or piece of data in your organization without (1) knowing where it is and (2) understanding it’s value. Security teams must identify potential weaknesses, assess vulnerabilities, and determine user roles and privilege levels. Organizations can assess potential vulnerabilities by identifying the devices that comprise their attack surface, which can include corporate firewalls and switches, network file servers, computers and laptops, mobile devices, printers and so on.
Organizations can then assess which users have access to data and resources and the level of access they possess. This helps them understand the particular behaviors of users and departments and classify attack vectors into categories like function and risk to make the list more manageable. Further, as the table below suggests, organizations can then leverage their risk management principles to find some acceptable level of risk using a variety of categories including threat intelligence and vulnerability criticality.
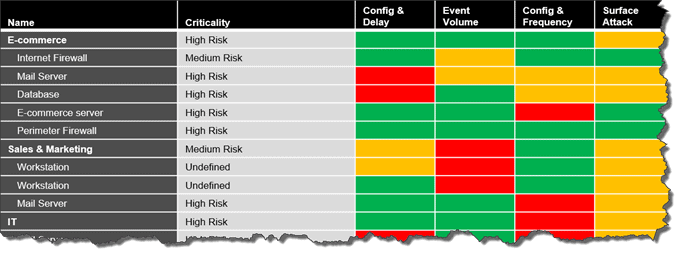
When it was discovered that Java, which is an application used on millions of devices had a critical vulnerability with a CVE score of 10 (only 30 vulnerabilities a year out of over 10,000 are scored a 10) security teams scrambled, almost in vain to patch every system that used the software. Many organizations had no idea whether the system they were patching had sensitive data or some critical function within the IT environment. They simply patched systems as quickly as possible without the full understanding that patching and testing all the systems in their environment would take weeks or even months. In the meantime, attackers were scanning their systems to find the vulnerability and exploit it. Many attacks were likely successful and threat actors may be lying in wait to exploit the most critical assets at some point in the future.
Consider this, the vulnerability is already being used by a “growing set of threat actors,” US Cybersecurity and Infrastructure Security Agency director Jen Easterly said in a statement on after the vulnerability was discovered. She added that the flaw is “one of the most serious I’ve seen in my entire career, if not the most serious” in a call with critical infrastructure operators on Monday in a call with news organizations. On that same call, a CISA official estimated that hundreds of millions of devices are likely affected.
Here are our 5 Key Lessons Learned in Managing Log4j / Log4Shell:
Tenable, the owner of the vulnerability scanner, Nessus and the industry leader on vulnerability assessment and management solutions found “organizations using a CVSS 7+ strategy to prioritize their remediation efforts waste 76% of their time remediating vulnerabilities that pose little to no risk—while leaving 44% of the riskiest vulnerabilities in their environment.
Hopefully the Log4j section illustrated how critical it is for organizations to stop wasting time on vulnerabilities that don’t pose risk. Security teams need to understand the full context of each vulnerability, including the criticality of affected assets and an assessment of current and likely future attacker activity. Thus, teams will be able to focus on what matters most, so you can take decisive action to reduce the greatest amount of business risk with the least amount of effort.
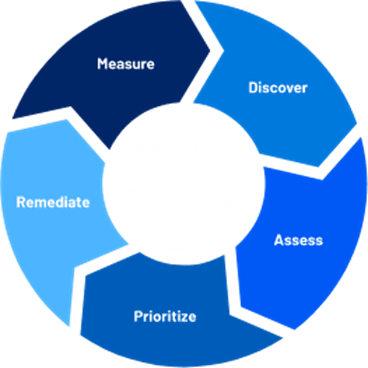
Figure 2 - Tenable's VM Lifecycle
A proactive, risk-driven approach delivers comprehensive, continuous visibility and informs technical and business decisions. The 4 steps to a successful vulnerability management program should be as follows:
In our last blog post we concluded by leveraging a statistic in the following study, Ponemon’s Digital Transformation and Cyber Risk study, which indicated that 82% of IT security and C-level executives experienced at least one data breach when implementing new technologies and expanding the supply chain. It is clear that organizations across industries will be challenged to secure the most valuable data available going forward.
We wanted to leverage that statistic to indicate how serious the issue of a sprawling attack surface will be for IT security leaders over the next several years. Identifying sensitive data, valuing systems, employing risk based patching and understanding potential threats will be critical for organizations to protect themselves and their customers.
To conclude this 4-part series we’d love to leave you with what we at Hitachi Systems Security feel our 5 steps IT security teams can take to reduce their attack surface and eliminate vulnerabilities effectively.
Regular network scans and risk-based patching enable organizations to quickly spot and eliminate potential vulnerabilities. It is vital to have full attack surface visibility to prevent issues with cloud and on-premises networks, as well as ensure only approved devices can access them. A complete scan must not only identify vulnerabilities but also show how endpoints can be exploited.
This severity value or CVE score of a vulnerability should be combined with system criticality and vulnerable exploitability to determine the risk that a particular vulnerability poses to an organization. This enables vulnerabilities to be ranked and triaged so that vulnerabilities that are most likely to cause significant damage to a critical system are handled as quickly as possible.
Unnecessary complexity can result in poor management and policy mistakes that enable cyber criminals to gain unauthorized access to corporate data. Organizations must disable unnecessary or unused software and devices and reduce the number of endpoints being used to simplify their network.
For example, complex systems can lead to users having access to resources they do not use, which widens the attack surface available to a hacker.
Network segmentation allows organizations to minimize the size of their attack surface by adding barriers that block attackers. These include tools like firewalls and strategies like microsegmentation, which divides the network into smaller units.
Employees are the first line of defense against cyberattacks. Providing them with regular cybersecurity awareness training will help them understand best practices, spot the telltale signs of an attack through phishing emails and social engineering.