
Global industries moving ahead with digital transformation innovation know ahead of time with each step towards a newer way of executing their new strategic direction comes a higher level of risk. Threats from the increase in DevOps security risks, secure access, and ransomware are some of the most common issues in a digital transformation project.
Transformation strategies involve the entire organization, including operations, human resources, IT, and product and service development. Organizations across all vertical markets, including government, transportation, healthcare, and construction, invest capital in planning and coordinating the transformation strategy to increase their digital capabilities.
In addition, as we suggested in our 4-Part Digital Transformation Blog Series earlier, “the term “Digital Transformation” has been and is being used to describe almost everything related to organizations adopting digital technologies to change business models, serve their customers through new channels, integrate with suppliers and partners and almost countless other benefits. With that in mind let’s start with a clear definition of what we feel describes digital transformation. Digital transformation is the process by which companies embed technologies across their businesses to drive fundamental change. The benefits? Increased efficiency, greater business agility, and, ultimately, the unlocking of new value for employees, customers, and shareholders. That definition is fairly broad, however, as we go forward, we’ll dig into the specifics of the types of technology organizations are adopting and add color to the various uses and benefits of the technology.”
Cyber breaches expose a higher risk to organizations' digital transformation strategies.
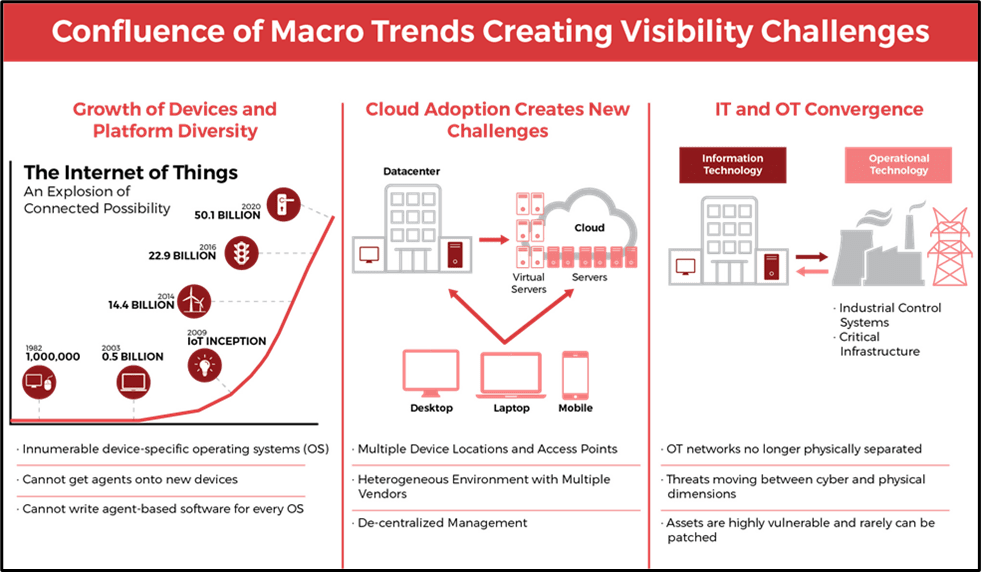 Figure 1 - IoT, Cloud and IT and OT Convergence will Change Business Models, Supply Chains, and Go-To-Market Strategies Dramatically
Figure 1 - IoT, Cloud and IT and OT Convergence will Change Business Models, Supply Chains, and Go-To-Market Strategies Dramatically
The digital transformation process (DX) is about an organization changing what they do, how they do it, and, more importantly, why they do it. DX transforms product creation, creating a new customer experience and integrating into a global supply chain for lower costs and greater operational efficiencies. Security transformation often is not part of the initial strategic planning process.
“There are very few companies that are building cyber and privacy risk management into their digital transformation,” said Sean Joyce, PriceWaterhouseCooper's US Cybersecurity and Privacy Leader, in response to PWC's 2018 Global State of Information Security Survey (GSISS), which was released earlier this year.
Still considered a cost by many in the corporate world, cybersecurity has quickly moved from a passive line-item expense to an asset on the company balance sheet. With the outbreaks of ransomware costing the organization millions in lost revenue, impact on the brand, and loss of trust among their client base, cybersecurity has slowly moved to be a critical asset to reduce the liability and risk to the organization.
Chief information security officers (CISO) and the chief information officer work with their internal peers to better under the business agility requirements within the digital business model strategy.
Each milestone gained within the DX strategy is a positive accomplishment for the organization. Migrating to a multi-cloud environment, optimizing artificial intelligence and machine learning for greater company data monetization, or leveraging global customer care services at a lower cost are examples of successful milestones. Enabling these success factors creates a higher cybersecurity risk with the addition of new attack surfaces.
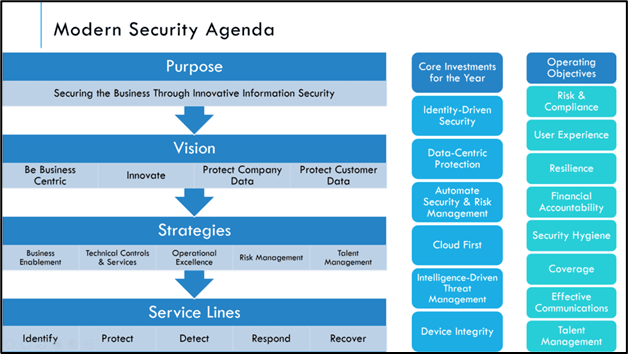
Figure 2 - This is an example of a modern security agenda that can be summarized in a single slide for the purpose of sharing with your executive team
Moving the organization to a cloud-native platform with less enhanced security could pose a considerable risk to the transformation strategy. Moving to a 100% managed services provider could impact the cost allocation, making the transformation unfeasible. These decisions have roots in the risk of increased cybersecurity breaches.
Digital transformation requires an investment in human capital. Software engineering, SecOps, DevOps, and NetSecOps engineers are in high demand. Organizations have changed their methods of recruiting talent for their digital transformation strategy. Many companies have leveraged several hiring portals to access highly qualified engineers in India, Vietnam, China, and Ukraine.
Many of these countries are home to many experienced software engineers. Specifically, in Ukraine, many software engineers trace their roots back to the Russian space federation.
Gaining access to global talent is much easier than years before. Becoming dependent on global resources also comes at a risk. Once war broke out between Russia and Ukraine, organizations are leveraging many of the software engineers living in these countries overnight needed to scramble to fill the void.
Cyclones, civil war, economic crisis, and COVID-19 all contribute to the risk of leveraging global resources.
As the organization is developing its strategic roadmap for its digital transformation projects, here are some critical workflows and sprints to properly integrate cybersecurity capabilities and resources:
These mandates could include:
Integrate every digital transformation milestone to include an engagement with a third-party penetration test firm. Determine the level of protection enabled after each milestone and feed the data into the enterprise risk management platform to determine the current organization-wide composite score.
Organizations evaluating a security approach to support digital transformation must consider which components of the current environment are portable to the new strategy. Many CIOs and CISOs have developed a parallel digital transformation strategy aligned with the master organizational-wide plan. Within IT, several legacy security, network, identity, and data management may end their useful life. CIOs should evaluate and consolidate current IT systems and operations into usable models to align with the company's digital transformation strategy.
*Transformation strategy - SD-WAN - Zero-trust- SASE - More organizations are transforming their remote connectivity by adding a critical layer to remote access to support ongoing WFH and secure remote access. By leveraging SD-WAN with Zero-trust, organizations can consolidate remote access with additional security while removing expensive redundant MPLS circuits while moving the security projection layer to the cloud for remote access consolidation.
*Transformation strategy - Enterprise-wide identity management platform with multi-factor authentication capabilities to support all connection requirements.
*Transformation strategy - Network containment and isolation is a proven security adaptive control to stop ransomware propagation laterally within the environment. While this capability prevents machines from infecting each other within the same layer two networks, existing network topologies must be re-designed with this capability embedded into the new architecture.
Many companies view cybersecurity expenditures as costs rather than investments. Based on the latest report from IBM, the price per breach, "data breach costs rose from USD 3.86 million to USD 4.24 million, the highest average total cost in the 17-year history of this report. Having cybersecurity into the fabric of digital transformation from the inception to post-enablement operations.
Actual cybersecurity events will disrupt the DX timeline, cost and resource model, and strategy. Without a clear understanding of the value and anticipated investment in cybersecurity, organizations waste value capital and resource time pursuing digital transformation projects.