
Most of us know what a Phishing attack is, however, I think it’s worthwhile to define the term and all of the different attacks that fall under the umbrella of the term Phishing. It is by far the number one attack vector and despite billions of dollars of investment in cybersecurity technology, Phishing will continue to be successful because Phishing attacks take advantage of human, um, let’s say flaws.
In a benchmark survey of 600 IT Security professional, Palo Alto’s Unit 42 incident response findings suggested, “77% of intrusions are suspected to be caused by three initial access vectors – phishing, exploitation of known software vulnerabilities, and brute-force credential attacks focused primarily on remote desktop protocol.” The report further suggested, “BEC is the leading and still growing attack tactic, with victim losses increasing by over 100% last year.” The U.S. Federal Bureau of Investigation calls BEC (Business E-mail Compromise) the “$43 billion scam,” referring to statistics for incidents reported to the Internet Crime Complaint Center from 2016-2021. A nice summary of the summary can be found here - Ransomware and Business Email Compromise (BEC) Account for 70% of Breaches. This is not a malicious phishing link…we promise.
Typically, whether a phishing campaign is targeted or sent to as many victims as possible, it starts with a malicious email message. The attack is often disguised as a message from a legitimate company or person. The more aspects of the message that mimic the real company, the more likely an attacker will be successful. The image below is an actual Phishing e-mail that was incredibly successful for a variety of reasons. The Bank of America branding is pretty darn good and the link that the e-mail is trying to persuade the user to click looks legitimate, despite the fact if the user hovered over the link with their mouse, they would find that the link and the URL do not match. That obviously just one of several issues that a smart, educated user would spot if they received this e-mail.

Just like we see in the Bank of America Phishing scam an attacker’s goals vary, but usually, the aim is to steal personal information or credentials. An attack often leverages a sense of urgency in the message, which could threaten account suspension, money loss or loss of the targeted the user’s job. Many victims tricked into an attacker’s demands rarely take the time to consider the request of the attacker.
Phishing continually evolves to bypass security and human detection; thus, organizations must be vigilant about social engineering training for staff and identify any new Phishing campaigns. It only takes one employee to click on a malicious link to allow an attacker entry into the organization’s network.
Phishing Attacks are Often Disguised E-mails
Phishing scams do far more damage to organizations than most non-security folks realize. This attack vector has several variations hackers will use to spread malware and ransomware, along with stealing users' login credentials. Phishing attacks also lead to the theft of intellectual property and personal information, including social security numbers and bank account information.
Phishing and fake emails are designed to lure the victim into performing an act based on rogue instructions from hackers and cybercriminals. As we said in the Bank of America example, these instructions could include clicking on a URL link leading to a malicious website, requesting the victim to send out a file, or even asking the user to go to a new password-changing site and update their credentials. Hackers are pretty darn smart at their craft – they create legitimate looking sites, users click on a link like we used in the Bank of America example, and they enter their username, password, birthdate, social security number and other personal information and the cyber criminals have it.
Like the AT&T example above, many email fraud attacks originate with a phishing email. Many hackers will use data collected on social networks and reverse social engineering techniques to contact potential victims. Many elements within the phishing email may originate from someone's LinkedIn or Facebook account.
Another example of a successful Phishing campaign may go like this, "Hey Mary, it is Steve from accounting. We went to St. Joe's high school together! Good to see you again! Hey, please update your corporate password when you have a quick moment. Please click the link below! Great to see you again. Let's grab a coffee sometime!"
This standard email message arrives in Mary's email box among dozens of others in a day and Mary innocently sends here corporate password to a criminal. Corporations often struggle with end users and phishing attempts because no matter how much they spend on cyber defense technology or how much training they provide employees, the organization’s defense is only as strong as its weakest link. Many users like Mary will simply read the potentially harmless email, click on the malicious link and open the door for attackers to move through the corporate network laterally to find the most sensitive information.
Types of Phishing Attacks
Part of the challenge of dealing with phishing attacks is the methods often change. Here are some common types of phishing emails:
Unfortunately, there are a lot more Phishing tactics but in the interest of time I simply list the most prominent. For clarity, here is an example of a successful phishing attack leveraging barrel and double barrel phishing method:
"Lewis, Mike here from IT. Welcome to the company. When you have a quick second, please change your password! Thanks, and welcome, signed Mike." The hacker is luring the potential victim by providing false sense of security.
A short time later, a second email arrives in Lewis's email:
"Lewis, hey man, I asked nicely, change your password now. It is a corporate policy, and you are not starting your first day on a good note. Click here at this link and change it, or I need to send a message to your director. Your Choice! signed Mike."
Notice the quick change in tone. The hacker is exploiting a new hire to force them to click on malicious links. How did the hacker know this person was new? Many cyber criminals and hackers will search social media for people posting their details, including "I got landed my dream job." Think about Linked-in for a second – the most viewed push messages that come from Linked-in are “Congratulate John Doe on starting a new position as Vice President of Super Bank International.”
Hackers continue to create new phishing messages to keep the incident response and SecOps teams off-balance. The consistent theme around each phishing method is preying on the weakness of the users.
Email phishing is effective by attacking and infecting one host or user. Ransomware attacks spread laterally through the network in an east-west direction. Most of the east-west attacks start with a single host.
Often Phishing attacks start with an attachment which could be a web page, a shell script (e.g., PowerShell), or a Microsoft Office document with a malicious macro. The macro and scripts can be used to download malware or trick users into divulging their account credentials.
Attackers register domains that look similar to the official domain of the company or occasionally use generic providers such as Gmail. Spoofed senders are possible with email protocols, but most recipient servers use email security that detects spoofed email headers. When users receive emails, the messages might use the official company logo, but the sender address would not include the official company domain as we saw in the Bank of America Phishing scheme.
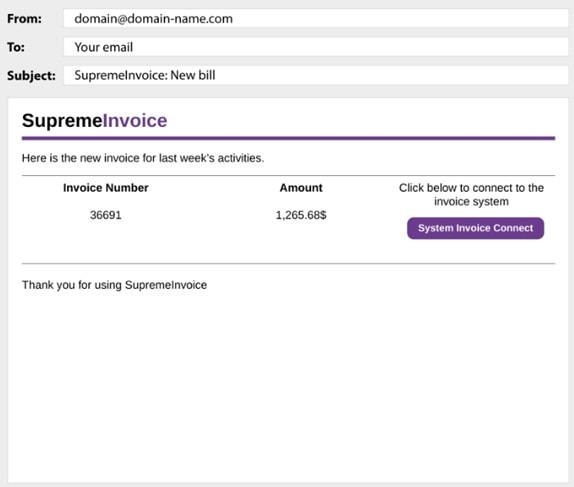
The button in the example opens a web page with a fraudulent Google authentication form. The page attempts to scam targeted victims into entering their Google credentials so that attackers can steal accounts.
Another method attackers use is to pretend they are internal help desk or technical support. The email asks users to install a messaging system, an application with hidden malware or run a script that will download ransomware.
One of the most prevalent attacks leverage malicious attachments that may look like legitimate file attachments like Word, Excel, of PDF’s, however, they are infected with malware that can compromise computers and their files. In the case of ransomware, all of the files on a PC could become locked and inaccessible. Or a keystroke logger could be installed to track everything a user types, including passwords. It’s also important to realize that ransomware and malware infections can spread laterally from one system or PC/Laptop to other networked devices, such as external hard drives, servers, and even cloud systems. I told you; these guys are sneaky and never seem to run out of tricks.
Prevention and Containment of Phishing Attacks
There are preventive strategies organizations should enable to help reduce the impact of a phishing attack and resulting malware and ransomware attack.
Along with email security and awareness controls, many organizations are investing in containment strategies to stop ransomware propagation. Once an end-user clicks on a rogue attachment or malicious link, the kill chain of a ransomware attack starts. Leveraging network-based containment, organizations get to force all communications from each host back to the gateway of last resort. The secured gateway can block all non-standard or undefined port and protocol communications. Ransomware propagations attempting to travel east to west will be stopped at the gateway. Ransomware propagation is contained unless the infected host is communicating the approved port and protocol.
Conclusion
Phishing protection is an important security measure companies can take to prevent phishing attacks on their employees and organization. As we suggested earlier, security awareness training and education around red flags when an email looks or feels suspicious definitely helps to reduce the likelihood folks fall for a fraudulent e-mail.
In addition, some email gateway reputation-based solutions can catch and classify phishing emails based on the known bad reputation of the embedded URLs. The downside is that these solutions often miss the well-crafted phishing messages with URLs from compromised legitimate websites that don’t have a bad reputation at the time of email delivery.
The most effective e-mail security solutions identify suspicious emails based on anomalytics, which look for unusual patterns in traffic to identify suspicious emails, then rewrites the URL and places surveillance or a constant watch on the URL for in-page exploits and downloads. These e-mail monitoring solutions have the ability to quarantine suspicious email messages. Administrators can the conduct research prior to letting a suspicious e-mail go to an end-user. Finally, if a high number of phishing emails are detected, administrators can alert employees, thus reducing the chance that a malicious link or file is clicked on.
Email phishing attacks are successful if the end-users continue to click or reply to suspicious emails. Leveraging email security solutions, security awareness training, and containment is a proven strategy to reduce the impact of phishing attacks. Many phishing attacks will find a way to exploit the user, either through social engineering, email threats, or even through voice phishing. Teaching the users to recognize the characteristics of a business email compromise, identifying a fake call from the IRS, or even a double barrel phish attack should be an ongoing strategy and part of the organization's culture.
If you think you’re the target of a phishing campaign report it to IT security or the Help Desk in your organization. For certain, on a corporate network, it’s best to report it to IT staff to review the message and determine if it’s a targeted campaign. For individuals, you can report fraud and phishing to the FTC.